19 min read
The Beginner's Guide to Multi-party Computation (MPC)
Welcome to our comprehensive guide on Multi-Party Computation (MPC), a transformative technology reshaping the landscape of data privacy and collaborative computation. In the digital era, where data security and privacy are paramount, understanding MPC is essential for professionals across various industries, from finance and healthcare to technology and beyond. This page serves as your in-depth guide to MPC, designed to cater to both beginners and those looking to expand their knowledge in this dynamic field.
As we navigate through this pillar page, we will cover various aspects of MPC:
- Understanding the Basics: Grasping the fundamental concepts and workings of MPC.
- Applications and Use Cases: Exploring how MPC is being applied in different sectors and its impact on real-world scenarios.
- Benefits and Challenges: Weighing the advantages and potential hurdles in the adoption of MPC.
- The Future Outlook: Looking ahead at the advancements, trends, and future potential of MPC.
This guide is structured to provide a holistic understanding of MPC, from its theoretical underpinnings to practical applications and future prospects. Whether you're a business leader, a data security expert, a policy maker, or simply a curious learner, this guide will equip you with a comprehensive understanding of MPC and its significance in today's data-driven world.
What is Multi-Party Computation?
At its core, Multi-Party Computation (MPC) is a subfield of cryptography that allows multiple parties to jointly compute a function over their inputs while keeping those inputs private. The essence of MPC is to enable this collaborative computation without any single party having access to the others' data.
The Birth and Evolution of MPC
MPC emerged from the field of cryptography in the 1980s. It was initially a theoretical concept, but over the years, it has evolved significantly, driven by both advances in computational power and a growing need for data privacy.
Basic Principles of MPC
Secret Sharing
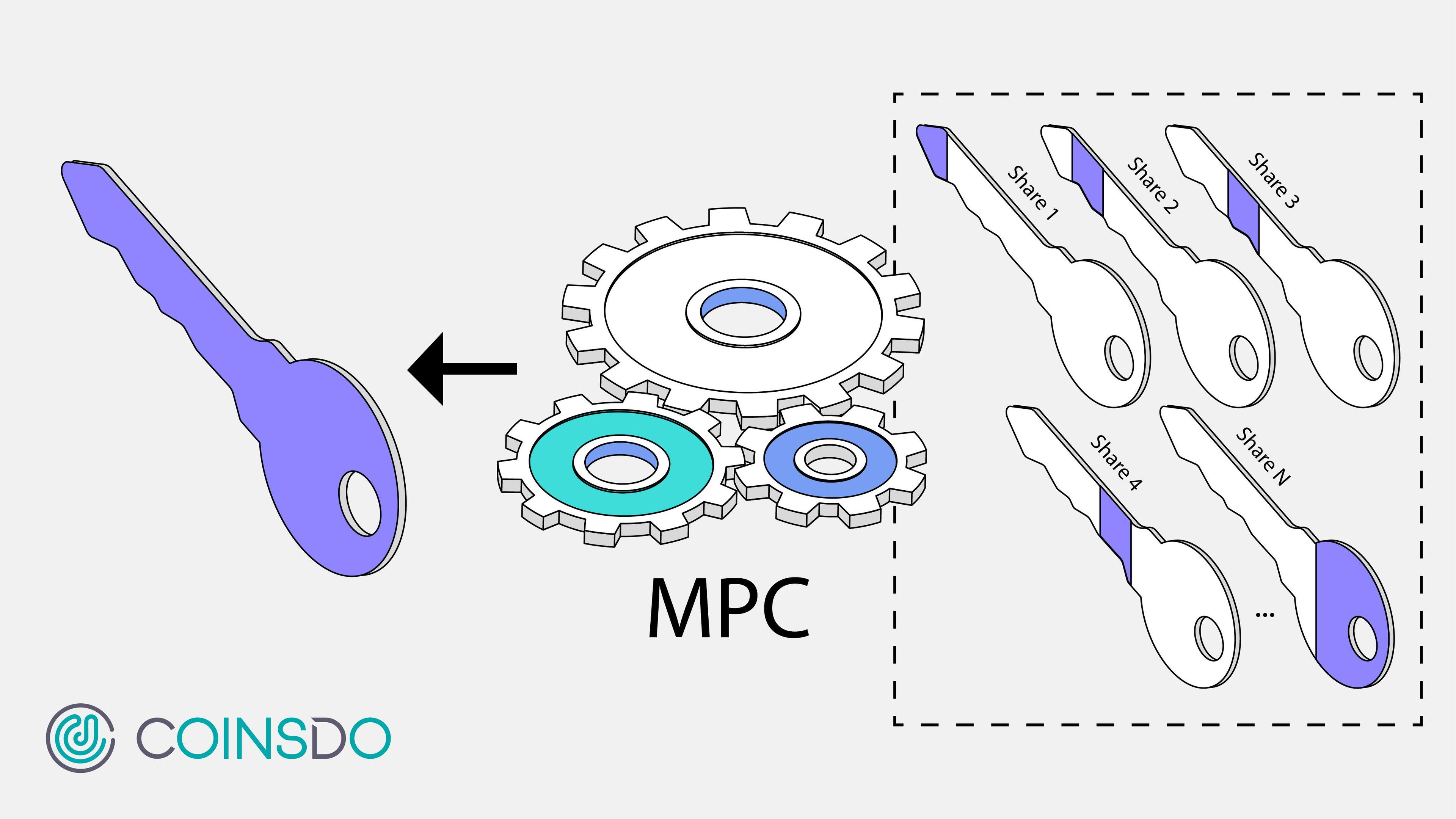
Secret sharing is a cryptographic protocol that plays a pivotal role in ensuring data privacy and security. It involves dividing a secret, such as a cryptographic key or a piece of sensitive information, into multiple parts, known as shares. These shares are then distributed among a group of participants. The key aspect of secret sharing is that the original secret can only be reconstructed when a sufficient number of these shares are combined together. This threshold is predetermined and ensures that no single participant can access the full secret on their own.
Here are 2 of the most common secret sharing schemes in use today:
Shamir's Secret Sharing Scheme
Developed by Adi Shamir in 1979, this is one of the most widely used secret sharing schemes. It is based on polynomial interpolation in finite fields. In Shamir's scheme, the secret is transformed into a polynomial of degree d, where d is one less than the number of shares required to reconstruct the secret (this is also known as the threshold). For instance, if the threshold is 3, the polynomial will be of degree 2. Each share is a point on this polynomial. To reconstruct the original secret, a minimum number of shares equal to the threshold is required. These shares are used to interpolate the polynomial, and the secret is the constant term of this polynomial.
Think of Shamir's method as a jigsaw puzzle. You have a picture (which is your secret) and you break it into many puzzle pieces. You give each friend a piece of the puzzle. Only when enough friends (the number you decide, like 3 or 4) come together and join their pieces, can they see the whole picture and find out the secret. If they have fewer pieces than needed, they can't see the full picture, so they can't guess the secret.
Blakley's Secret Sharing Scheme
Proposed by George Blakley around the same time as Shamir's, this scheme is based on geometric properties. In Blakley's method, the secret is represented as a point in an n-dimensional space. Each share corresponds to a hyperplane in this space. The intersection of at least n such hyperplanes (where
n is the threshold) is a single point, which is the secret. Much like Shamir's method, unless the threshold number of hyperplanes (shares) is available, the secret cannot be determined. Blakley’s scheme is notable for its simplicity and the fact that it offers a different mathematical approach to secret sharing, rooted in geometric concepts.
Blakley's method is like having a treasure map. You draw lines on the map, and where enough lines cross, that's where the treasure (your secret) is hidden. You give each friend a different line to add to the map. Only when enough friends (again, a number you decide) come together and draw their lines on the map, will they find the crossing point where the treasure is hidden. If not enough friends come together, they won't find the crossing point and can't find the treasure.
Computational Trust
Computational trust refers to the reliance on mathematical algorithms and protocols to establish and verify trust in digital environments. Unlike traditional trust, which is often based on personal experiences and subjective judgment, computational trust is built upon objective, algorithmically driven processes.
In the context of blockchain technology, computational trust is exemplified by the use of cryptographic techniques and consensus algorithms. For instance, cryptographic methods like public and private key encryption ensure that transactions are secure and that identities are authenticated, thereby creating a trust layer over digital interactions. MPC itself is a cryptographic technique that distributes trust among multiple parties. No single party can compromise the computation or the privacy of the data.
Additionally, consensus mechanisms, such as Proof of Work (PoW) or Proof of Stake (PoS), further reinforce trust. These mechanisms allow a network of decentralized and often anonymous participants to agree on the validity of transactions without needing a central authority, thus creating a trustless environment where participants can engage securely based on the assurance provided by the computational processes themselves.
Real-World Example
Let's consider a few simple, real-world examples.
Imagine a company with multiple departments like Research, Marketing, and Operations, each managing its own budget. To enhance security in treasury operations, they use a blockchain wallet with Multi-Party Computation (MPC) for managing funds. The wallet's private key is split into key shards using MPC, with each department head holding a shard. When a department needs to access funds, heads from at least two departments must collaboratively use their key shards to authorize the transaction. This setup not only bolsters security, preventing unauthorized access even if one shard is compromised, but also ensures shared control and responsibility over company finances, streamlining operation and enhancing collaborative decision-making.
Also, imagine three schools trying to find out the average salary of their teachers to ensure competitive pay scales, but without revealing the actual salaries of individual teachers. Using MPC, each school can input its salary data into a shared computation system. The system will then calculate the average salary and reveal only this figure to all three schools. No school learns about the specific salary details of teachers from the other schools, thus maintaining confidentiality.
How Does MPC Work?
Multi-Party Computation (MPC) might sound like a concept straight out of a science fiction novel, but its workings are grounded in solid mathematical and cryptographic principles. To understand how MPC functions, let's break it down into more digestible parts.
The MPC Process
Step 1: Input Gathering
Each participant has their private data (input). In our earlier example of schools calculating average salaries, each school's input is its own set of salary data.
Step 2: Data Fragmentation
This private data is then fragmented into pieces, using cryptographic techniques. Think of it like taking a sentence (your data) and cutting it into individual words or letters (fragments) that, on their own, make little sense.
Step 3: Distributing Fragments
These fragments are distributed among all participating parties. Each party holds a piece of the puzzle, but not enough to see the entire picture.
Step 4: Computation on Fragments
The parties then perform computations on their fragments. This is akin to each party solving a small part of a larger puzzle without knowing what the puzzle is.
Step 5: Result Compilation
Finally, the fragments of the computed result are brought together to reveal the outcome – in our case, the average salary – without exposing any individual salaries.
Benefits and Challenges of Multi-Party Computation (MPC)
Multi-Party Computation (MPC) stands at the forefront of data privacy and security, offering a unique set of benefits and challenges. This technology is pivotal in enabling secure, collaborative computation while safeguarding sensitive data.
Benefits of MPC
Enhanced Data Privacy and Security
MPC ensures that individual data inputs remain confidential, even during joint computations. This is crucial in sectors like healthcare and finance, where data sensitivity is high. By not revealing individual inputs, MPC protects sensitive information, making it a robust tool against data breaches and unauthorized access.
Collaborative Computation Without Compromising Data Integrity
Entities can leverage collective data insights without exposing their own data sets, fostering collaboration in fields like medical research and secure voting systems. This collaborative approach enhances business efficiency and societal advancements by pooling resources and knowledge.
Challenges of MPC
Computational Complexity
The process of data fragmentation and secure computation in MPC is resource-intensive, often requiring significant computational power, which can lead to increased costs and operational challenges. This complexity can result in latency issues, particularly in applications that require real-time processing.
Scalability Issues
The efficiency of MPC protocols can decrease as more participants join the computation, posing a challenge for large-scale applications. Balancing the number of participants with the computational load and response time is a key challenge in MPC scalability.
Security Considerations
While MPC enhances data security, it is not immune to all risks. The distributed nature of computation can introduce new vulnerabilities, especially if protocols are not rigorously designed.
Continuous research and development are required to identify and mitigate potential security threats in MPC systems.
The Future of Multi-Party Computation (MPC)
The trajectory of Multi-Party Computation (MPC) is not just a linear path of technological advancement; it's a burgeoning field poised to redefine the boundaries of privacy, security, and collaborative computation. As we peer into the future, several trends, potential applications, and innovations stand out, signaling a transformative phase for MPC.
Current Trends in MPC Research and Development
Enhanced Efficiency and Scalability
Researchers are making strides in optimizing MPC protocols for better efficiency and scalability. This involves innovative algorithmic improvements to reduce computational load and latency, making MPC more practical for real-time applications.
Integration with Emerging Technologies
The fusion of MPC with technologies like blockchain, IoT, and AI is opening new frontiers. For instance, integrating MPC with AI can lead to the development of privacy-preserving machine learning models where data can be used without being exposed.
Potential Future Applications
Broadening Data Privacy
As global data privacy regulations tighten, MPC could become a go-to solution for compliant data processing. Its ability to analyze data without exposing it aligns perfectly with the principles of privacy-by-design in software development.
Revolutionizing Online Voting
MPC can provide the backbone for secure and anonymous digital voting systems, potentially increasing voter participation while maintaining the integrity of the electoral process.
Advancements and Innovations
User-Friendly MPC Platforms
The development of more intuitive MPC platforms is on the horizon. These platforms aim to lower the barrier to entry, allowing non-experts to harness the power of MPC for their privacy and security needs.
Cross-Disciplinary Applications
Beyond tech-centric applications, MPC is finding its place in diverse fields. For example, in the legal field, MPC can enable confidential collaboration on sensitive cases without revealing privileged information.
Getting Started with Multi-Party Computation (MPC)
Embarking on the journey of understanding and utilizing Multi-Party Computation (MPC) can be both exciting and daunting. Whether you're a budding researcher, a tech professional, or just an enthusiast, getting started with MPC requires access to the right resources and communities. This section aims to provide a roadmap for those new to MPC, offering guidance on educational resources, communities for collaboration and discussion, and practical tips for beginners.
Educational Resources
Books and Academic Papers
Start with foundational texts and research papers that lay the groundwork for MPC. Look for works by pioneers in the field, which often provide both historical context and detailed explanations of core concepts.
Here are a few of our recommendations:
Secure Multiparty Computation and Secret Sharing 1st Edition
A Pragmatic Introduction to Secure Multi-Party Computation
Online Courses and Tutorials
Numerous online platforms offer courses ranging from introductory to advanced levels. These courses often include practical examples and hands-on projects that can help solidify your understanding.
Webinars and Workshops
Keep an eye out for MPC-focused sessions conducted by universities and tech organizations. These can provide insights into current research and applications.
Communities and Forums
Online Forums and Discussion Groups
Platforms like Reddit, Stack Overflow, and specialized cryptography forums are great places to ask questions, share knowledge, and stay updated on the latest in MPC.
Professional Networks and Conferences
Joining professional networks and attending conferences can connect you with experts and peers in the field. These events are often a hub for sharing cutting-edge research and practical implementations.
Tips for Beginners
Start with the Basics
Ensure a strong grasp of basic cryptographic concepts before diving deep into MPC. A solid foundation is key to understanding more complex topics.
Hands-On Practice
Apply what you learn through small projects or simulations. There are several open-source MPC frameworks and tools available. Experimenting with these can provide practical insights and help build technical skills. Practical experience is invaluable in understanding the nuances of MPC.
Stay Curious and Updated
The field of MPC is rapidly evolving. Stay curious, keep learning, and stay abreast of new developments and breakthroughs. Keep track of the work being done by leading researchers and institutions in MPC. Their publications, blogs, and talks can be a rich source of advanced knowledge and inspiration.
Embracing the Future with Multi-Party Computation (MPC)
As we conclude this comprehensive exploration of Multi-Party Computation (MPC), it's clear that MPC is not just a cryptographic curiosity, but a pivotal technology shaping the future of data privacy and collaborative computation. From its theoretical underpinnings to its burgeoning array of applications, MPC stands as a testament to the incredible potential of combining mathematics, cryptography, and computer science to address some of the most pressing challenges of our digital age.
The journey through the various facets of MPC - its principles, applications, benefits, challenges, and future prospects - reveals a technology that is both powerful and nuanced. MPC offers a path to a world where collaborative data analysis and decision-making can occur without sacrificing individual privacy or data security. This is more than just a technological advancement; it's a step towards a more secure and privacy-conscious society.
As MPC continues to evolve and integrate into various sectors, the importance of understanding and engaging with this technology cannot be overstated. For professionals, researchers, and enthusiasts alike, MPC represents a field of endless possibilities and opportunities. Whether it's in enhancing the security of financial transactions, protecting sensitive medical data, or enabling private and secure global collaborations, MPC has a role to play.
In closing, this pillar page on Multi-Party Computation serves as both a starting point and an invitation. An invitation to delve deeper into a field that is redefining the boundaries of what's possible in data security and privacy. As we stand on the brink of a new era of digital innovation, MPC is a key player, and its journey is one that we should all be keen to follow and participate in.